|
Size: 4440
Comment: Validity and key use and Display with tofu + pgp / easygpg
|
Size: 12636
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 1: | Line 1: |
| = Validity and Opportunistc encryption = | ## page was renamed from EasyGpg2016/Validity <<TableOfContents>> = Automated Encryption = |
| Line 4: | Line 7: |
| opportunistic mail encryption when using the trust-model tofu+pgp. == Concept of "Verified Communication partner" (Signatures) == |
opportunistic mail encryption and how to use the trust-model tofu+pgp for automated encryption. == TODO: == Things to do after discussion and Feedback not integrated in this draft * The yellow checker does not work as a symbol. * Level 5 is not part of the screenshots. == Trust Levels === * Level 0 (Validity Unknown): With trust-model tofu+pgp this is only for Keys that were never used before to verify a signature. Key should not be used for opportunistic encryption. * Level 1 (Validity Marginal && Touf.validity < Key with enough history for basic trust): This level means that have some confidence that the recipient actually can use the key as we have seen at least one signature or we have a weak trust path over the WOT. It's OK to use that Key for Opportunistic encryption but when receiving a signed message we should only show in details that a message was signed and don't make assumptions about the senders identity. There may be some indication that the sender demonstrated a willingness to use crypto mails, especially if opportunistic encryption is disabled. * Level 2 (Validity Marginal && ((Tofu.validity >= Key with enough history for basic trust && signfirst > 3 Days ago) || Key retrieved through slightly authenticated source (e.g. WKD)): We have some basic confidence that the Sender is who he claims because we either have an established communication history or the source of the key (e.g. the mail provider) provided the key for this sender. This is the highest level you can achieve without user interaction. * Level 3 (Validity Full): This is reached either through Web of Trust or if a user explicitly set the tofu Policy to "Good" for this key. High confidence. Automatically this Level can only be reached through WoT. * Level 4 (Direct Trust): A key that is ultimately trusted has signed this key. Either yourself or someone that is allowed to make that e.g. your central "CA" style person you may have in an organisation. === Rationale === === Won't many Levels hurt Usability? === The "automated user" that never fiddles with GnuPG will only see Level one and Level two. With level one being nearly presented as an "Unsigned" mail the "Basic Trust" will be the only level that is really visible. For more advanced users and from a "Ui Language" point of view only two levels would be too simplistic because we have to distinguish still between just automatic Trust based on history. and trust from Web of Trust or manual checks. Without a manual check we can never fully claim that the senders identity was verified. So with need an additional level for manually checked keys and offer that option e.g. from a details dialog. So that a user can mark "Ok with this communication partner I want to be absolutely sure that I'm always using the right key. So I manually verify the fingerprint.". That's a *can* it should not be suggested that this needs to be done, but it should be offered. The additional Level's also give flexibility for Organisational Measures like: You may only send restricted documents to Directly trusted keys. === Why the time delay for level 2? === The idea is to make it more expensive for an attacker to reach level 2 as we then start to make claims about the attacker. An attack that is kept up over some time is more difficult. Especially if it involves some external factors, like a phishing website etc. that might be turned of. It also gives others the chance to intervene if they detect an attack. It also mitigates User Experience problems arising from the use of the encryption count in GnuPG's calculation for basic history because if you encrypt 20 drafts or 20 mails quickly to the same key it should not become level 2 before you have seen a signature. A concern is that using the time of the first signature verifcation before reaching level 2 make lead to bad user experience. E.g.: You look at the same message after three days. Now it's level 2, last time you looked it was level 1. == Signature Status == |
| Line 10: | Line 91: |
| * Is there additional information that the sender is really is the indended communication partner. This could be displayed as a green checker or a seal ribbon or something. It should be prominent and next to the signed content. |
* Is there additional information that the sender is really is the intended communication partner. (Level 2 + Level 3) This could be displayed as a checker or a seal ribbon or something. It should be prominent and next to the signed content. There should be a distinction between Levels two and three but it may be slight. |
| Line 18: | Line 101: |
| sender is not verified it should be displayed the same as an unsigned mail because | sender is not verified it should be displayed similar to an unsigned mail because |
| Line 20: | Line 103: |
| Communication partner. | Communication partner. You may want to show a tofu Conflict more prominent as user interaction is required at this point. Especially: **ignore GPGME's Red suggestion** An attacker would have removed the signature instead of invalidating it. It should be treated like an unsigned mail and only additional info in details should be shown for diagnostic purposes. Similarly when Red is set because a key is expired or so. It's not more negative then a unsigned mail. |
| Line 30: | Line 120: |
| === Definition of Sender === * Mail: The Sender is the first UID where the mailbox matches the mailbox of the {{{From header}}}. * File: The Sender is the UID from the {{{Signer's User ID}}} subpacket of a signature. === Definition of Verified Sender === A sender is only verified if the signature was made by a key that contains a UID for the Sender and one of the conditions match: * The signature is Fully / Ultimately valid. * The signature is marginally valid and: ** The signcount shows that there were several signed messages exchanged involving this key. The current threshold for this is at least **ten** messages. == Opportunistic Encryption (Mail only) == A MUA should offer automated opportunistic encryption. To determine if a mail can be sent encrypted one of the following rules must match for each recipient: * There is a Fully / Ulitimately valid key for the recipient. * This is a marginally valid key for the recpient and the first UserID matches |
== Conflict handling == A tofu conflict means that you have seen two keys for a userid and that the keys are not cross-signed and both are valid. When can this happen: Attacks: # There is a man in the middle trying to intercept encrypted communication. # There is an impostor trying to claim a false identity. # There is a D~O~S attacker trying to hurt usability so much that automated encryption is no longer used. Misuse: # A user generated two keys e.g. on two devices and did not cross sign them and uses both. # A user lost control of his old key, and did not have a revocation certitifcate. The first misuse case should be handled on the senders side. The second misuse case may be handled or mitigated by using slightliy authenticated source for the key retrieval. === Resolving conflicts on the senders side === A tofu aware ~G~U~I should (even when TOFU is disabled) check when a secret key is used for signing if there are other secret keys with the same uid available and they are not cross signed a GUI should offer that option. Similarly, if a signature is verified by a mua and there are secret keys available with the same userid and they are not cross signed this should be told to the user and offered to do if possible. ==== WKD Checks ==== A tofu aware ~G~U~I should check when signing or from time to time if a different key is uploaded to a WKD for this userid and warn in that case. This will also make a permanent man in the middle attack by a mail service provider more expensive as it would mean providing a different key to the attacked user then to others. === Resolving conflicts on the receivers side === We will have to see in practice how often tofu conflicts happen and if there are different means we can avoid them. For now the preferred solution is the Conflict Dialog. An alternative approach for discussion is the automated resolution. Resolution through a conflict Dialog hurts the goal to automate encryption. The goal should be to try hard to avoid it. ==== Conflict Dialog ==== A dialog should be offered that asks the user to check with the sender / call his IT Support and then: * Use the new key from now on. (Policy auto on the new Key, Policy bad on the old key) * Reject the new key (Policy bad on the new key, Policy auto on the old key) {{{ The key used to secure this message differs from the key usually used to secure messages from "foo@example.com" Please call "foo@example.com" or your IT Support to call what happend and check if the new key to secure your communication with him has the fingerprint: 1101 C077 198C 91E3 5BB9 CC78 856B 9E7E 60A1 542A Secure communication with "foo@example.com" is no longer possible until you have ensured that the new key is legitimate. [Ask me later] [Use new key] [Keep using the old key] }}} There should be no option to mark both keys as "good" this case needs to be handled on the sender side to avoid that this becomes common practice and many uses that communicate with the sender run into a conflict. ==== Automated Resolution ==== A conflict could be automatically resolved by keeping the old key in use and treating the new key for validity display just like a fresh key. Technically this is not planned for in the TOFU trust model, but this is an idea for discussion and could be implemented in a MUA. Probably by setting policy to good for both keys and handling that specially in validity display. The conflict would be detectable in the interface for a user who cares about it because it will no longer be shown that the sender is somewhat verified and that there is no basic history yet. Meaning the sender is back to level 1. This necessitates an option to mark the old key explicitly as bad. E.g if your communication partner has lost his old key through misuse. But that would then be needed to be triggered by the sender when he receives replies that he can't decrypt. With the assumption that the sender already knows more about what happened and can explain this then to the recipient. ===== How would this relate to attacks? ===== * A man in the Middle attack will be cheaper because it won't require manual interaction of the user. (This is partly mitigated by keeping the old key in use for encryption.) * Impostor attack would still be prevented until the impostor has built up enough communication history. * The DOS Crypto Attack will be prevented as conflicts are not shown so prominent. ===== Opinion of aheinecke: ===== While I like the idea of still keeping to use the old key in case of conflict as it moves the misuse problems from the receiver to the sender and the usage of the old key will mitigate a Man in the Middle, as a first step automated conflict resolution is a step too far, we need to see if false positive conflicts are really a thing in practice and then think in a next step about automated resolution. Automated encryption already "lowers" security compared to the theoretical web of trust, (Imo not compared to the wot as used in practice) and it might lead to bad publicity and won't be accepted by the existing community. So my conclusion here is that this goes a step too far. == Key discovery and Opportunistic Encryption (Mail only) == A MUA should offer automated key discovery and opportunistic encryption. The WKD / WKS helps with automated key discovery and should be used (by using {{{--locate-key}}}) To determine if a mail can be sent automatically encrypted one of the following rules must match for each recipient: * There is a Fully / Ultimately valid key for the recipient. * This is a marginally valid key for the recipient and the first UserID that matches |
| Line 53: | Line 259: |
| key was obtained through a slightly authenticated source. === Marginal Substates === For Marginal keys there should be a visible hint that the recipient's key might not be the intended recipient. E.g. a Lock symbol with different overlays for warning, yellow checker, green checker. These substates should indicate: * Very little confidence (marginal + signcount < 10) * Basic confidence (marignal + signcount >= 10) * Good confidence (marginal + signcount >= 100) === Definition of slightly authenticated source === A slightly authenticated source is a key from a source that gives some confidence in the fact that a recipient controls the key obtained from the source. It does **not** influence the status of Verified Sender more then seeing one signed message of that sender. The slightly authenticated source should just help determining an automatically selected key for opportunistic encryption that shows an indication that the recipient controls the key exactly as if you would have already seen one message signed with that key. === Keys from public keyservers === If you recieve a message from an Unknown Key a MUA should automatically retrieve it from a public keyserver or a Web Key directory. This Key can then be used for opportunistic encryption. == Examples from GpgOL == The Information boxes in the screenshots only open when a user hovers over the Icon. A click on the Signature Icon should open a Key Details dialog with further information about a key and e.g. options for conflict handling. A web of trust verified sender: {{http://files.intevation.de/users/aheinecke/gpgol_sigs/trusted.png}} A tofu verified sender: {{http://files.intevation.de/users/aheinecke/gpgol_sigs/tofu.png}} A marginal signature without enough history: {{http://files.intevation.de/users/aheinecke/gpgol_sigs/tofu-untrusted.png}} An invalid signature: {{http://files.intevation.de/users/aheinecke/gpgol_sigs/invalid.png}} An unsigned mail: {{http://files.intevation.de/users/aheinecke/gpgol_sigs/unsigned.png}} |
key was obtained through a slightly authenticated source (e.g. WKD). === Auto Key Retrieve === Additionally to WKD lookup, if you receive a message from an Unknown Key a MUA should automatically retrieve it from a public keyserver or a Web Key directory. This Key can then be used for opportunistic encryption because you have seen a signature it is very likely that the recipient can decrypt. (auto-key-retrieve in gnupg) == Screenshots from GpgOL == {{gpgol-no-key.png}} No key was found. Level 0. {{gpgol-tofu-first.png}} The first signed message form someone else. Level 1. {{gpgol-tofu-second.png}} The second message. Level 1. {{gpgol-tofu-basic.png}} Basic trust! Level 2. {{gpgol-tofu-fully.png}} Full trust! Level 3. {{gpgol-invalid-sig.png}} Invalid sig. Level 0. {{gpgol-conflict.png}} Tofu conflict. User attention required. |
Contents
Automated Encryption
This page is intended as a discussion base for validity display and opportunistic mail encryption and how to use the trust-model tofu+pgp for automated encryption.
TODO:
Things to do after discussion and Feedback not integrated in this draft
- The yellow checker does not work as a symbol.
- Level 5 is not part of the screenshots.
Trust Levels
- Level 0 (Validity Unknown): With trust-model tofu+pgp this is only for Keys that were never used before to verify a signature. Key should not be used for opportunistic encryption.
- Level 1 (Validity Marginal && Touf.validity < Key with enough history for basic trust): This level means that have some confidence that the recipient actually can use the key as we have seen at least one signature or we have a weak trust path over the WOT. It's OK to use that Key for Opportunistic encryption but when receiving a signed message we should only show in details that a message was signed and don't make assumptions about the senders identity. There may be some indication that the sender demonstrated a willingness to use crypto mails, especially if opportunistic encryption is disabled.
- Level 2 (Validity Marginal && ((Tofu.validity >= Key with enough history for basic trust && signfirst > 3 Days ago) || Key retrieved through slightly authenticated source (e.g. WKD)): We have some basic confidence that the Sender is who he claims because we either have an established communication history or the source of the key (e.g. the mail provider) provided the key for this sender. This is the highest level you can achieve without user interaction.
- Level 3 (Validity Full): This is reached either through Web of Trust or if a user explicitly set the tofu Policy to "Good" for this key. High confidence. Automatically this Level can only be reached through WoT.
- Level 4 (Direct Trust): A key that is ultimately trusted has signed this key. Either yourself or someone that is allowed to make that e.g. your central "CA" style person you may have in an organisation.
Rationale
Won't many Levels hurt Usability?
The "automated user" that never fiddles with GnuPG will only see Level one and Level two. With level one being nearly presented as an "Unsigned" mail the "Basic Trust" will be the only level that is really visible.
For more advanced users and from a "Ui Language" point of view only two levels would be too simplistic because we have to distinguish still between just automatic Trust based on history. and trust from Web of Trust or manual checks.
Without a manual check we can never fully claim that the senders identity was verified. So with need an additional level for manually checked keys and offer that option e.g. from a details dialog. So that a user can mark "Ok with this communication partner I want to be absolutely sure that I'm always using the right key. So I manually verify the fingerprint.".
That's a *can* it should not be suggested that this needs to be done, but it should be offered.
The additional Level's also give flexibility for Organisational Measures like: You may only send restricted documents to Directly trusted keys.
Why the time delay for level 2?
The idea is to make it more expensive for an attacker to reach level 2 as we then start to make claims about the attacker. An attack that is kept up over some time is more difficult. Especially if it involves some external factors, like a phishing website etc. that might be turned of. It also gives others the chance to intervene if they detect an attack.
It also mitigates User Experience problems arising from the use of the encryption count in GnuPG's calculation for basic history because if you encrypt 20 drafts or 20 mails quickly to the same key it should not become level 2 before you have seen a signature.
A concern is that using the time of the first signature verifcation before reaching level 2 make lead to bad user experience. E.g.: You look at the same message after three days. Now it's level 2, last time you looked it was level 1.
Signature Status
There should only be one prominent information when reading a signed mail:
- Is there additional information that the sender is really is the intended communication partner. (Level 2 + Level 3)
This could be displayed as a checker or a seal ribbon or something. It should be prominent and next to the signed content. There should be a distinction between Levels two and three but it may be slight.
Don't treat signed mails worse then an unsigned mail
A MUA should not treat any signed mail worse then an unsigned mail. If a sender is not verified it should be displayed similar to an unsigned mail because in both cases you have no information that the Sender is actually your intended Communication partner. You may want to show a tofu Conflict more prominent as user interaction is required at this point.
Especially: ignore GPGME's Red suggestion An attacker would have removed the signature instead of invalidating it. It should be treated like an unsigned mail and only additional info in details should be shown for diagnostic purposes. Similarly when Red is set because a key is expired or so. It's not more negative then a unsigned mail.
Put it in Details
The information that a Mail was signed should of course be available even if the signature could not be used to verify the sender. And the user should get tips how to verify the sender (e.g. exchange fingerprints out of Band) but this should be "Details". Although easily accessible this should not be needed to establish cryptographically secured communication.
Conflict handling
A tofu conflict means that you have seen two keys for a userid and that the keys are not cross-signed and both are valid.
When can this happen:
Attacks:
- There is a man in the middle trying to intercept encrypted communication.
- There is an impostor trying to claim a false identity.
- There is a DOS attacker trying to hurt usability so much that automated encryption is no longer used.
Misuse:
- A user generated two keys e.g. on two devices and did not cross sign them and uses both.
- A user lost control of his old key, and did not have a revocation certitifcate.
The first misuse case should be handled on the senders side. The second misuse case may be handled or mitigated by using slightliy authenticated source for the key retrieval.
Resolving conflicts on the senders side
A tofu aware GUI should (even when TOFU is disabled) check when a secret key is used for signing if there are other secret keys with the same uid available and they are not cross signed a GUI should offer that option.
Similarly, if a signature is verified by a mua and there are secret keys available with the same userid and they are not cross signed this should be told to the user and offered to do if possible.
WKD Checks
A tofu aware GUI should check when signing or from time to time if a different key is uploaded to a WKD for this userid and warn in that case. This will also make a permanent man in the middle attack by a mail service provider more expensive as it would mean providing a different key to the attacked user then to others.
Resolving conflicts on the receivers side
We will have to see in practice how often tofu conflicts happen and if there are different means we can avoid them. For now the preferred solution is the Conflict Dialog. An alternative approach for discussion is the automated resolution. Resolution through a conflict Dialog hurts the goal to automate encryption. The goal should be to try hard to avoid it.
Conflict Dialog
A dialog should be offered that asks the user to check with the sender / call his IT Support and then:
- Use the new key from now on. (Policy auto on the new Key, Policy bad on the old key)
- Reject the new key (Policy bad on the new key, Policy auto on the old key)
The key used to secure this message differs from the key usually used to secure
messages from "foo@example.com"
Please call "foo@example.com" or your IT Support to call what happend
and check if the new key to secure your communication with him has
the fingerprint:
1101 C077 198C 91E3 5BB9 CC78 856B 9E7E 60A1 542A
Secure communication with "foo@example.com" is no longer possible
until you have ensured that the new key is legitimate.
[Ask me later] [Use new key] [Keep using the old key]There should be no option to mark both keys as "good" this case needs to be handled on the sender side to avoid that this becomes common practice and many uses that communicate with the sender run into a conflict.
Automated Resolution
A conflict could be automatically resolved by keeping the old key in use and treating the new key for validity display just like a fresh key.
Technically this is not planned for in the TOFU trust model, but this is an idea for discussion and could be implemented in a MUA. Probably by setting policy to good for both keys and handling that specially in validity display.
The conflict would be detectable in the interface for a user who cares about it because it will no longer be shown that the sender is somewhat verified and that there is no basic history yet. Meaning the sender is back to level 1.
This necessitates an option to mark the old key explicitly as bad. E.g if your communication partner has lost his old key through misuse. But that would then be needed to be triggered by the sender when he receives replies that he can't decrypt. With the assumption that the sender already knows more about what happened and can explain this then to the recipient.
How would this relate to attacks?
- A man in the Middle attack will be cheaper because it won't require manual interaction of the user. (This is partly mitigated by keeping the old key in use for encryption.)
- Impostor attack would still be prevented until the impostor has built up enough communication history.
- The DOS Crypto Attack will be prevented as conflicts are not shown so prominent.
Opinion of aheinecke:
While I like the idea of still keeping to use the old key in case of conflict as it moves the misuse problems from the receiver to the sender and the usage of the old key will mitigate a Man in the Middle, as a first step automated conflict resolution is a step too far, we need to see if false positive conflicts are really a thing in practice and then think in a next step about automated resolution.
Automated encryption already "lowers" security compared to the theoretical web of trust, (Imo not compared to the wot as used in practice) and it might lead to bad publicity and won't be accepted by the existing community.
So my conclusion here is that this goes a step too far.
Key discovery and Opportunistic Encryption (Mail only)
A MUA should offer automated key discovery and opportunistic encryption. The WKD / WKS helps with automated key discovery and should be used (by using --locate-key)
To determine if a mail can be sent automatically encrypted one of the following rules must match for each recipient:
- There is a Fully / Ultimately valid key for the recipient.
- This is a marginally valid key for the recipient and the first UserID that matches the recipients mailbox has a signcount of at least one. Or the recipients key was obtained through a slightly authenticated source (e.g. WKD).
Auto Key Retrieve
Additionally to WKD lookup, if you receive a message from an Unknown Key a MUA should automatically retrieve it from a public keyserver or a Web Key directory. This Key can then be used for opportunistic encryption because you have seen a signature it is very likely that the recipient can decrypt. (auto-key-retrieve in gnupg)
Screenshots from GpgOL
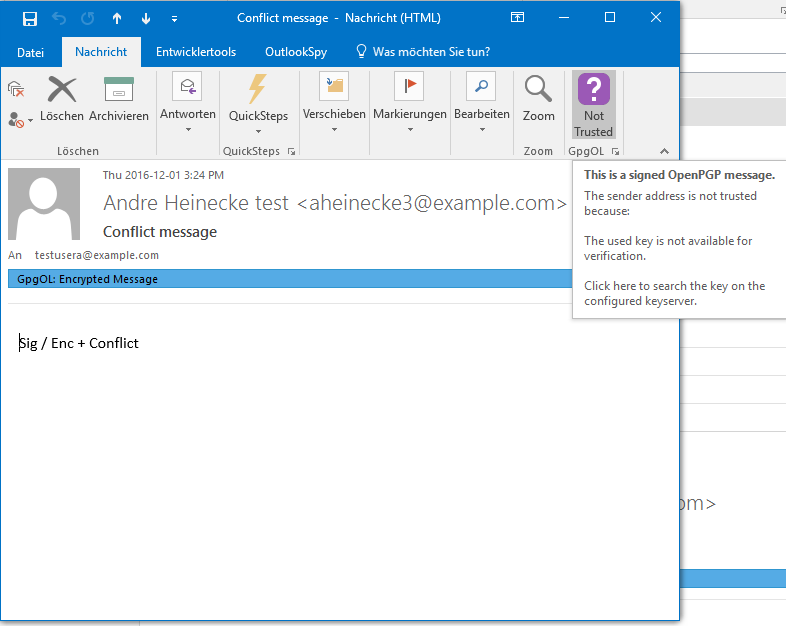
No key was found. Level 0.
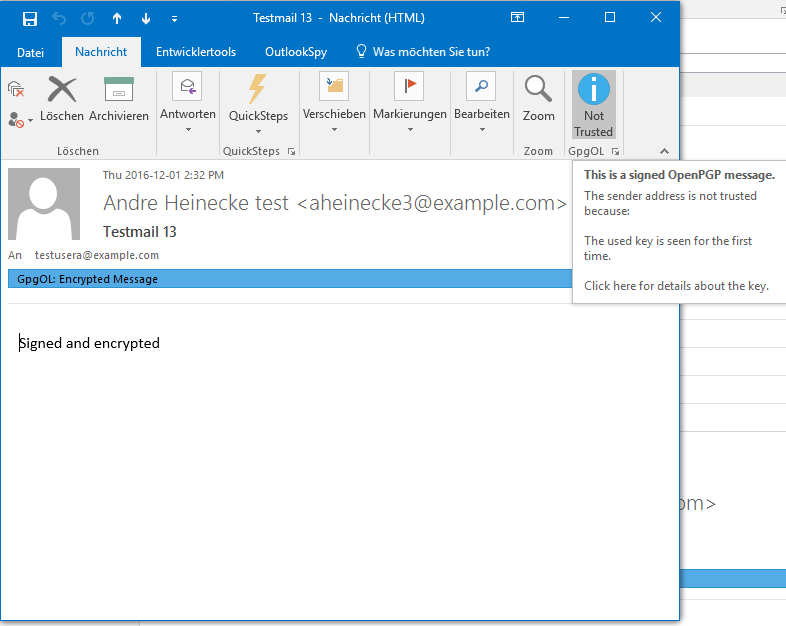
The first signed message form someone else. Level 1.
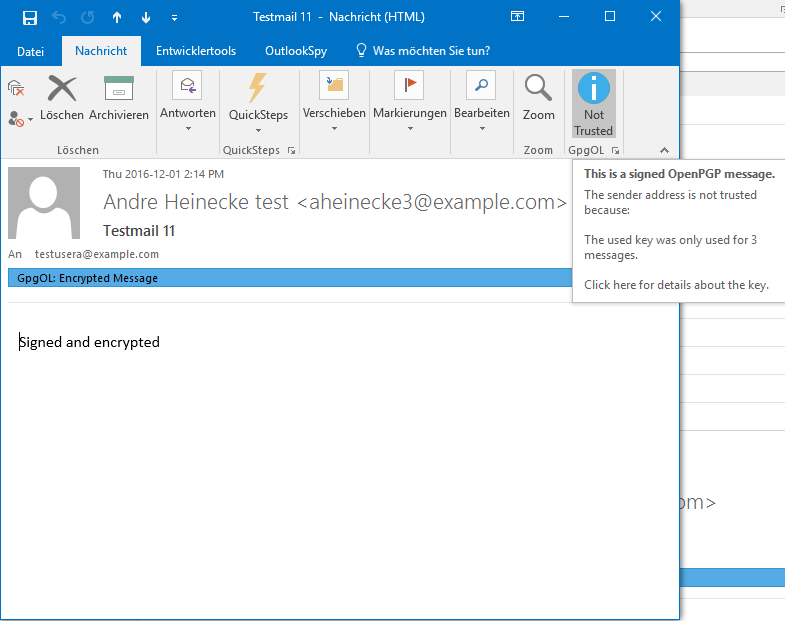
The second message. Level 1.
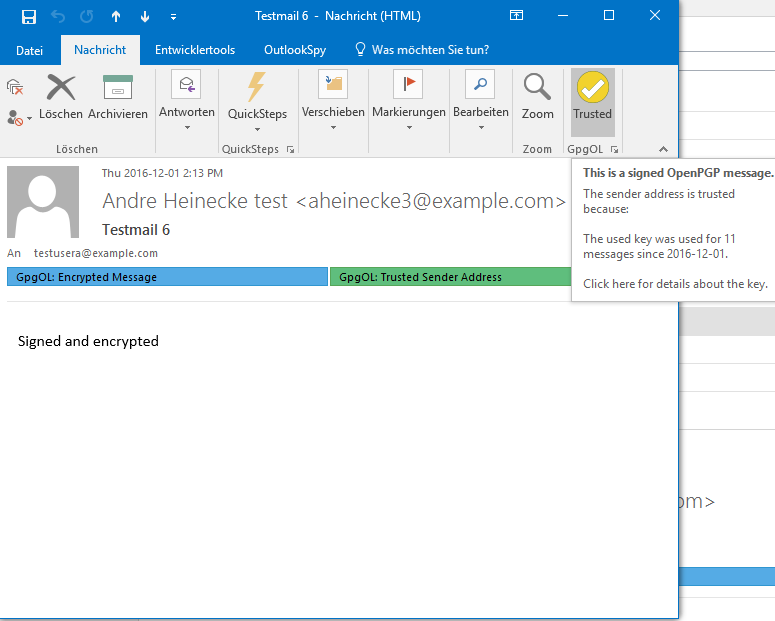
Basic trust! Level 2.
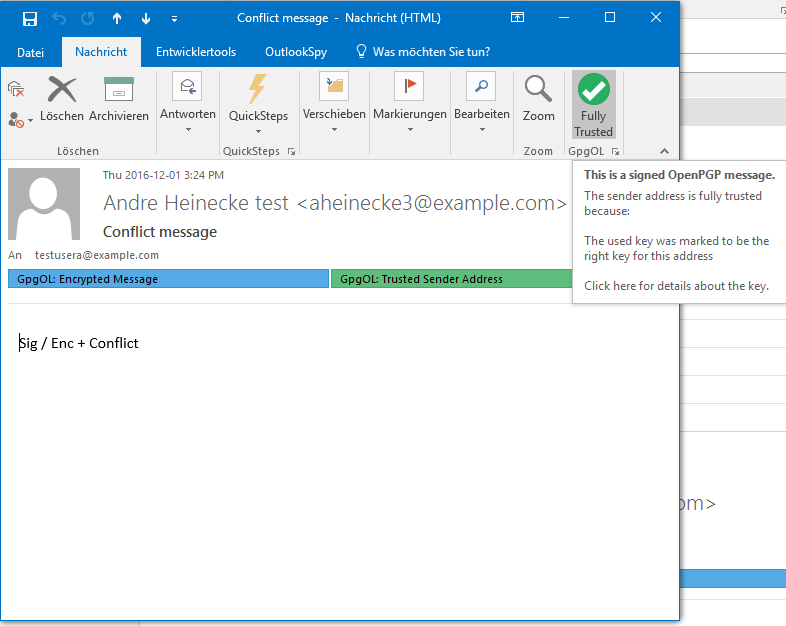
Full trust! Level 3.
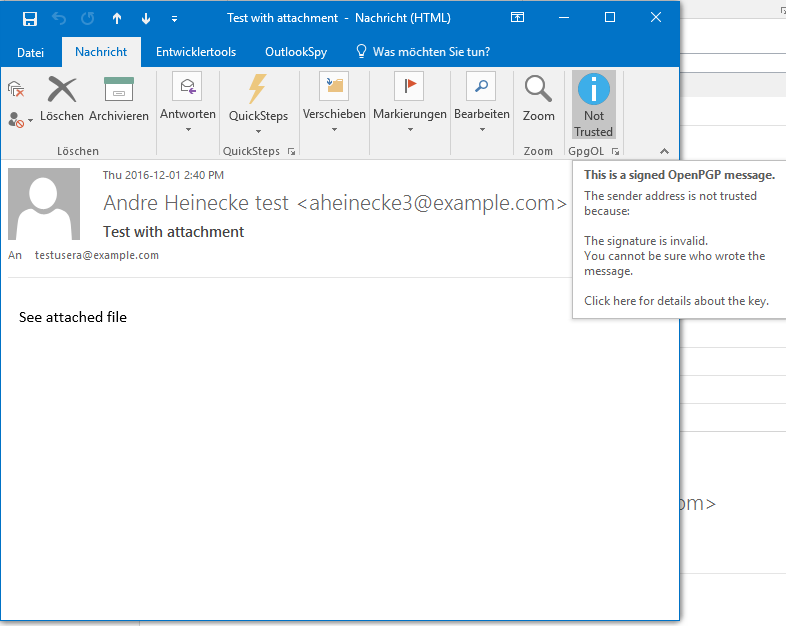
Invalid sig. Level 0.
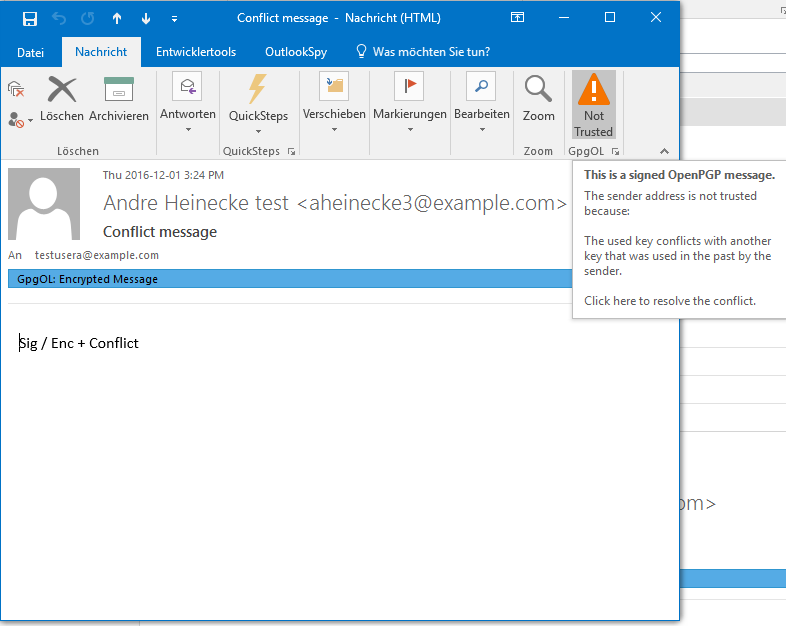
Tofu conflict. User attention required.
