Recommendations
- Turn off Subject "Encryption" (↓)
- Turn on crypto (↓)
- Use Web Key Directory (WKD) to search for pubkeys (↓)
- Use plain text emails
Overview
Thunderbird (since version 78 first released 2020-07) implements its own OpenPGP/MIME support, using the libraries RNP (https://github.com/rnpgp/rnp) and Botan.
The main advantage for Thunderbird users is that they do not have to install an additional application like Gpg4win on Windows. The main drawback is that Thunderbird has its own handling of key material which is separated from the rest of the operating system and other applications that are using GnuPG for example. Some abilities that GnuPG provides are missing, e.g. handling of hardware tokens like smartcards or USB devices.
Thunderbird can still be configured to use a system's GnuPG installation for private key operations see https://wiki.mozilla.org/Thunderbird:OpenPGP:Smartcards .
The Thunderbird people have an FAQ about the new OpenPGP support.
History
Until version 68 (last release 2020-10), Thunderbird did not have OpenPGP/MIME functionality included. The external extension Enigmail provided used GnuPG. A necessary and large change in how browser extensions can be implemented made Enigmail's technical implementation unfit for newer versions. See the explanation of Enigmail's maintainer. Enigmail's support for this version stopped 2021-10-01.
It is unknown what the main reasons for doing a new implementation instead of using GnuPG (and Gpg4win) were. One Mozilla developer wrote about licensing concerns, but other people have pointed out that GPGME is GNU LGPL and the GNU GPL of GnuPG itself allows for a combined distribution of Thunderbird and GnuPG.
Previously in 1999 and 2005, Mozilla rejected to include (already implemented) OpenPGP/MIME functionality because they were preferring S/MIME according to Werner Koch.
Hints
Disabling Experimental Subject Encryption
Thunderbird implements an experimental (non-standard) way that encrypts the normally unencrypted subject header line of an email, in a non-backward compatible way. This feature is active by default in Thunderbird.
Thunderbird replaces the subject of encrypted emails with three dots to protect users from accidentally disclosing sensitive information. So many other email clients will just see three dots like ... as the subject, where the sender added real information. Viewing emails with encrypted subjects in Thunderbird and other compatible email clients shows the original subject. Besides the loss of information, this feature may also break message filtering and searching on the server.
The GnuPG project recommends turning this feature off for the outlined reasons.
Disabling subject encryption
Thunderbird users may disable the feature by unchecking the option in the settings:
- Account settings
- Search the wanted account in the left pane
- End-To-End-Encryption
- Scroll to section Advanced settings
- Uncheck Encrypt the subject of OpenPGP messages
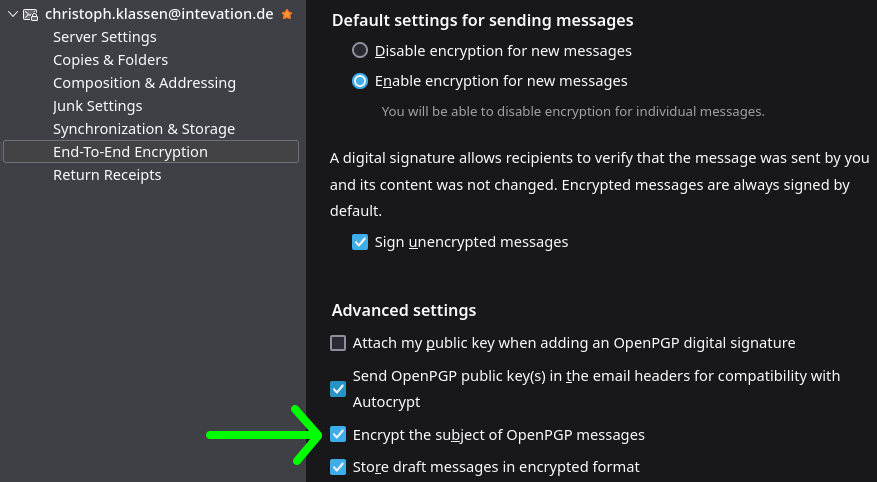
It is also possible to use the Config Editor. This way is only recommended for advanced users, the risk of breaking anything is high!
Search for the following entries and changing them from true to false:
- mail.identity.default.protectSubject
- mail.identity.id1.protectSubject
- and if you have multiple identities configured, repeat the last step for id2, id3, etc.
Administrators of Debian-based systems can set these values system-wide in a file /etc/thunderbird/pref/subjectencryption.js:
pref("mail.identity.default.protectSubject", false);
pref("mail.identity.id1.protectSubject", false);
...
Background
In general, The subject of an email is information about its transport. And transport information in a decentral network - just like the writing on the outside of a postal mail envelope - cannot be protected in principle. When reflecting on this, if you need confidentiality, choose a subject that is plausible in context, but without sensitive contents, to best veil potential unwanted observers. (Your thinking is right: The more sensitive this is, the more you have to build up a plausible context for your unavoidable traces first.)
Details
For the reason why Thunderbird's implementation is suboptimal, see January to March 2021 on gnupg-user, e.g.
- https://lists.gnupg.org/pipermail/gnupg-users/2021-February/064862.html
- https://lists.gnupg.org/pipermail/gnupg-users/2021-March/064981.html
- https://lists.gnupg.org/pipermail/gnupg-users/2021-February/064858.html
Instructions
How to enable encryption
Result after completing this instruction
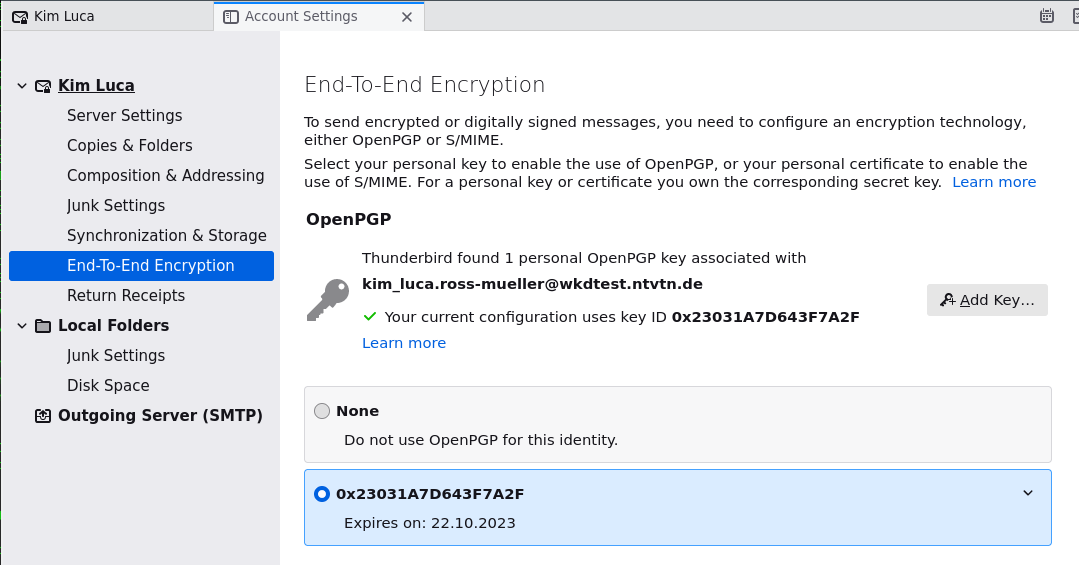
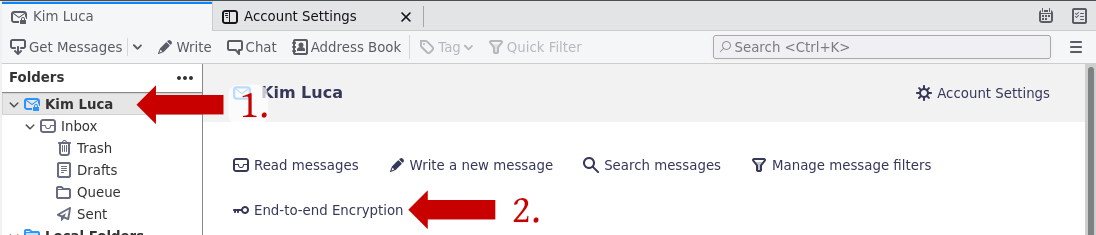
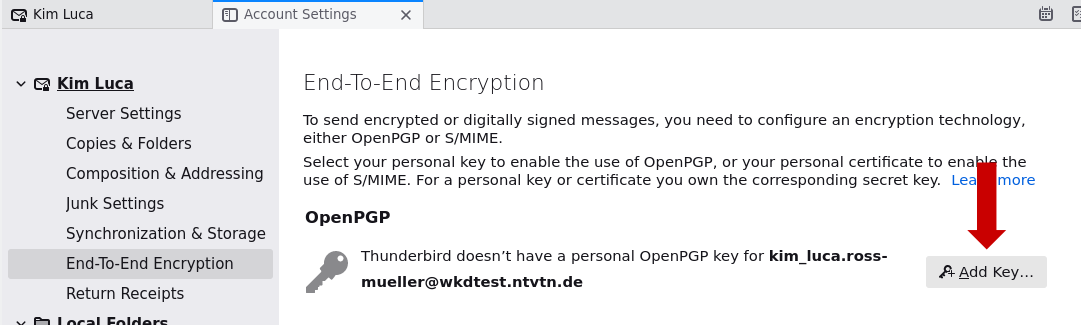
1. Click on the account name and then on "End-to-end Encryption"
2. Click on the button "Add Key..." on the right side of the window.
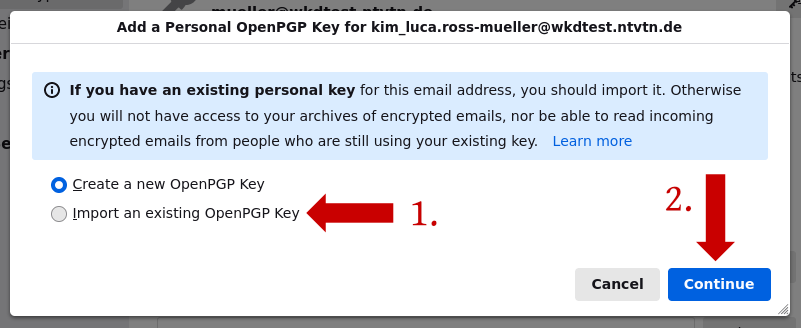
3. A window will be opened, where you can choose, if you want to import a key or to create a new key pair. In this instruction, we explain how to import an existing key. For that click on the option "Import an existing OpenPGP Key" and on the button "Continue".
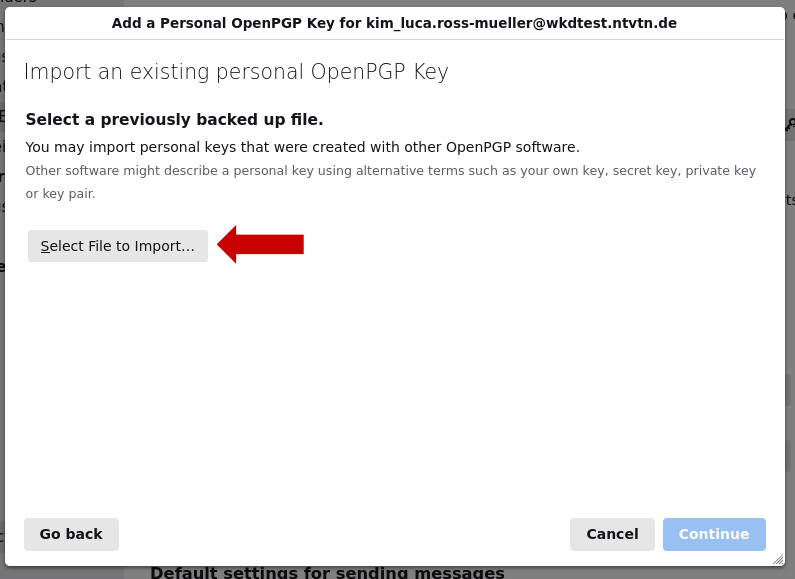
4. In the next window click on the button "Select File to Import...".
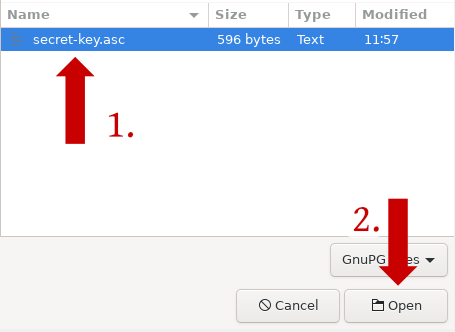
5. A window with the file manager appears. Here you have to navigate to the folder, where your key is in. Then select it and click on "Open".
6. Confirm with a click on "Continue".
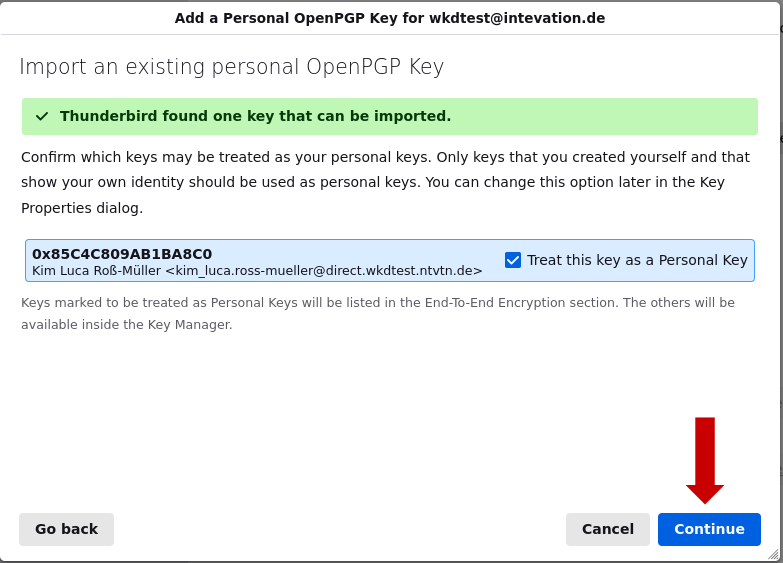
7. Enter the password for the key and click on "Sign in".
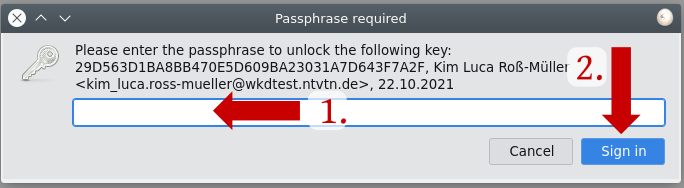
8. Confirm with a click on "Continue".
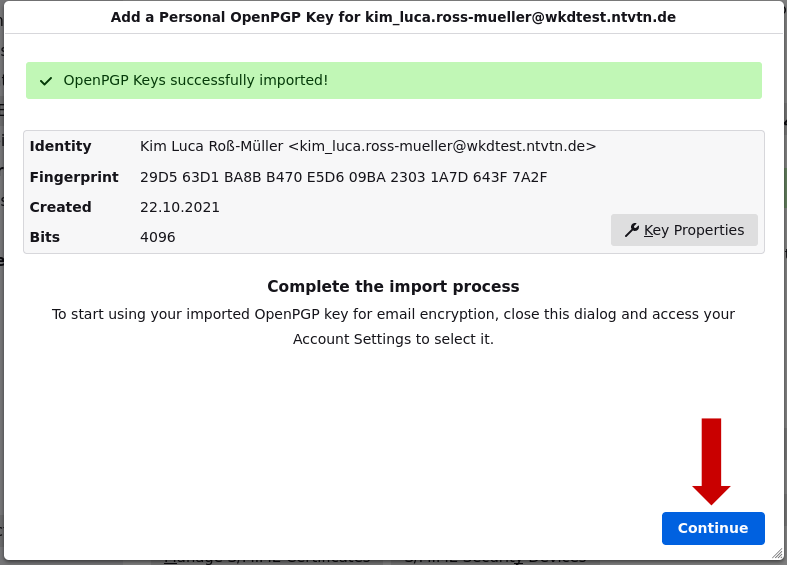
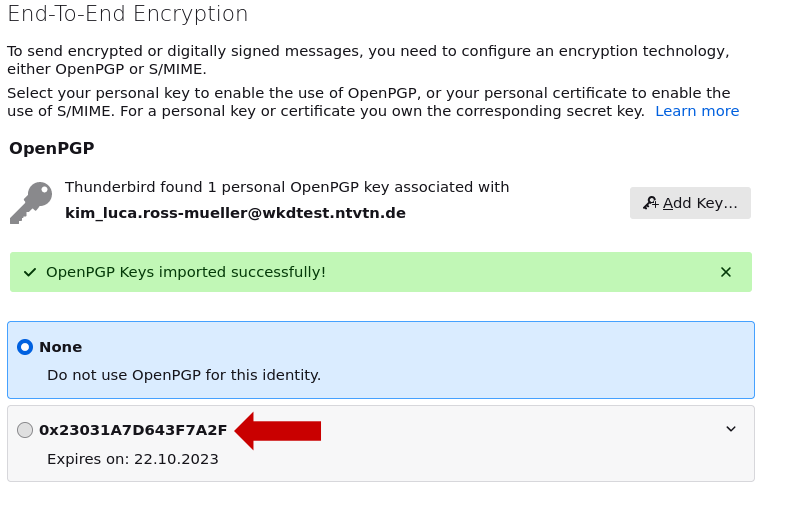
9. Now you have to select the imported key by clicking on it.
How to get a key via WKD
Version 128
Tested with version 128.6.0esr.
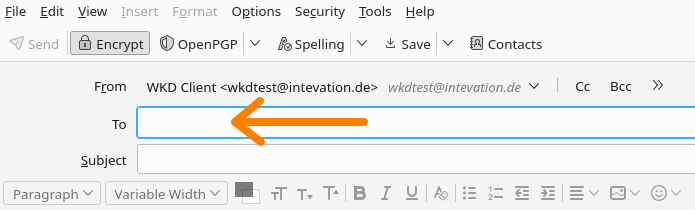
1. Open the window to compose an email
2. Enter an email address in the "To" field and press the Return button on your keyboard.
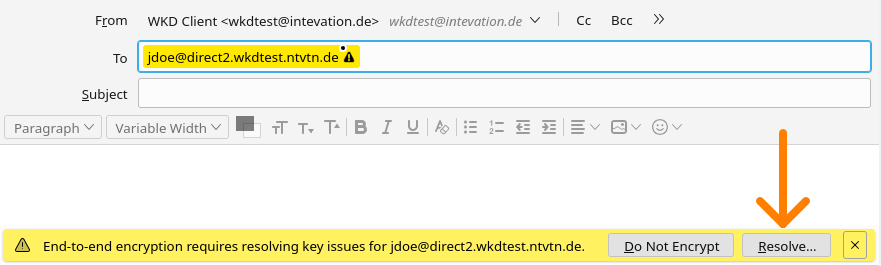
3. Click on the button "Resolve..."
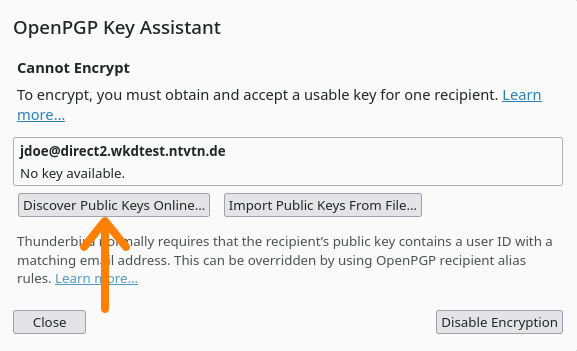
4. A new window appears. Click on "Discover Public Keys Online..."
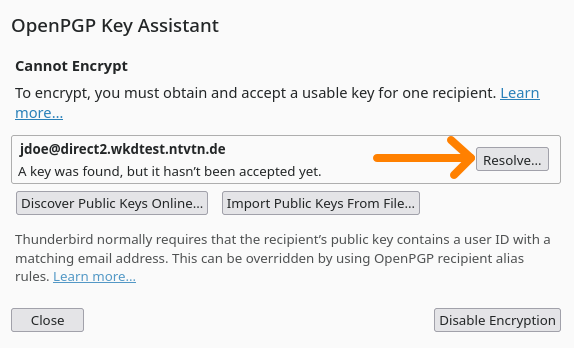
5. After a short loading animation click on "Resolve..." in the next window.
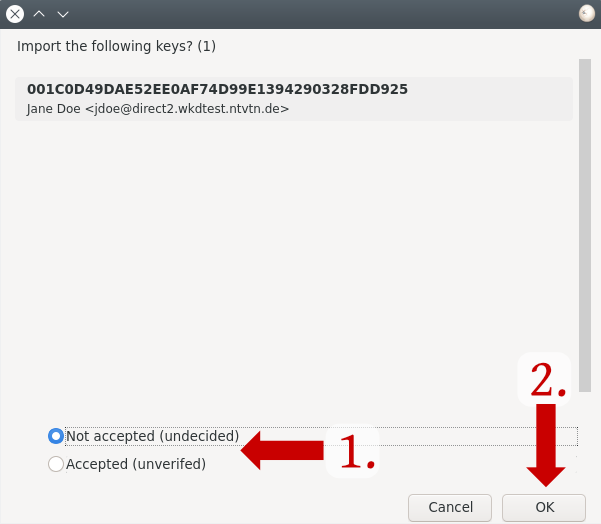
6. Select the key and click on "Accept"
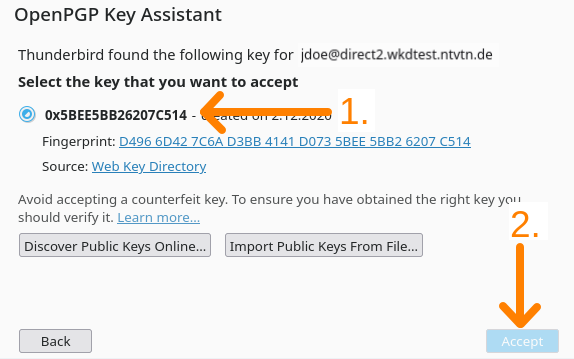
7. Click on "Close"
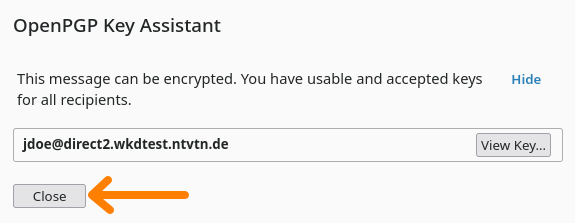
Now you can continue to write your email.
Version 115
1. Open the window to compose an email
2. Enter an email address and click on "security".
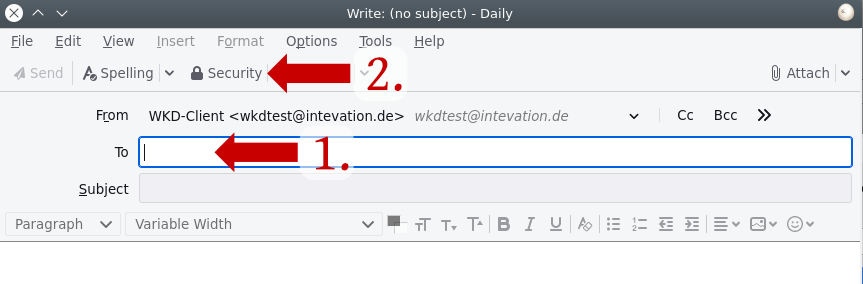
3. Select the address, whose key is missing and click on "Manage keys for selected recipient..."
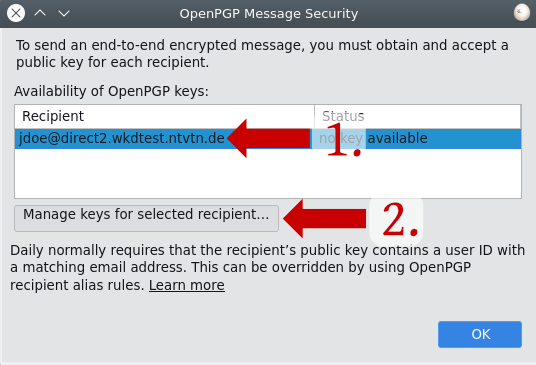
4. Click on "Discover new or updated key"
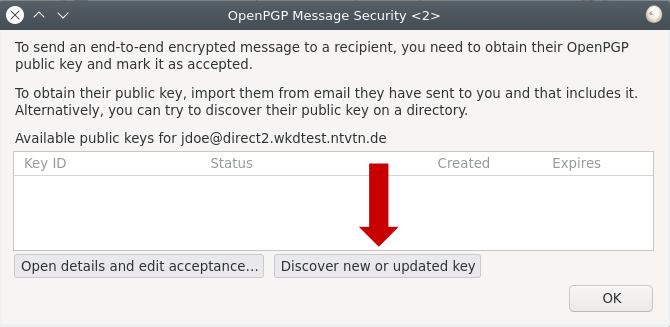
5. Choose, if you want to accept the key and click on "OK".