|
Size: 487
Comment: components
|
← Revision 8 as of 2016-05-20 08:10:19 ⇥
Size: 1718
Comment: typos
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 4: | Line 4: |
| The ~EasyGPG components: * email client (e.g. Kontact Mail, Thunderbird with Enigmail) |
The software components we plan to change or consider as part of the contract: * email clients (Kontact Mail and Thunderbird with Enigmail as example for others) |
| Line 7: | Line 7: |
| * email service provider | * a service located at the email service provider |
| Line 13: | Line 13: |
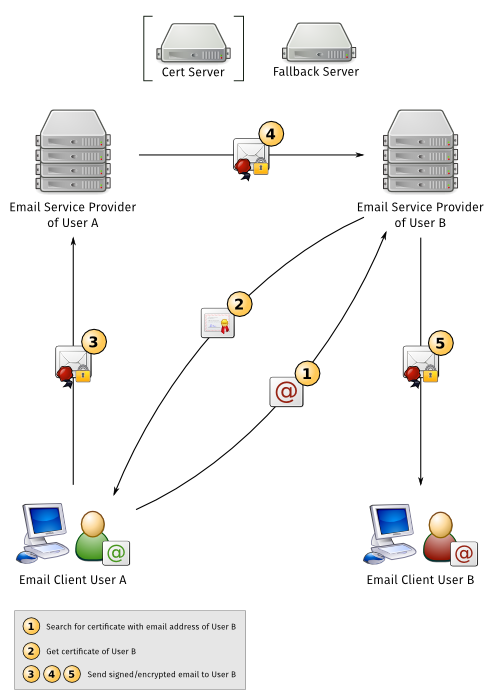
| == How EasyGPG based email client should work? | == How should an improved email client work? User A wants to send a signed/encrypted email to user B. A has only the email address of B. A's email client gets the OpenPGP (public) certificate from B's email service provider (step 1+2) which is used to encrypt the email to B. |
| Line 15: | Line 17: |
| [[attachment:easygpg-send-email.pdf|PDF]] | [[attachment:easygpg-send-email.pdf|PDF]] [[attachment:easygpg-send-email.svg|SVG]] |
| Line 17: | Line 19: |
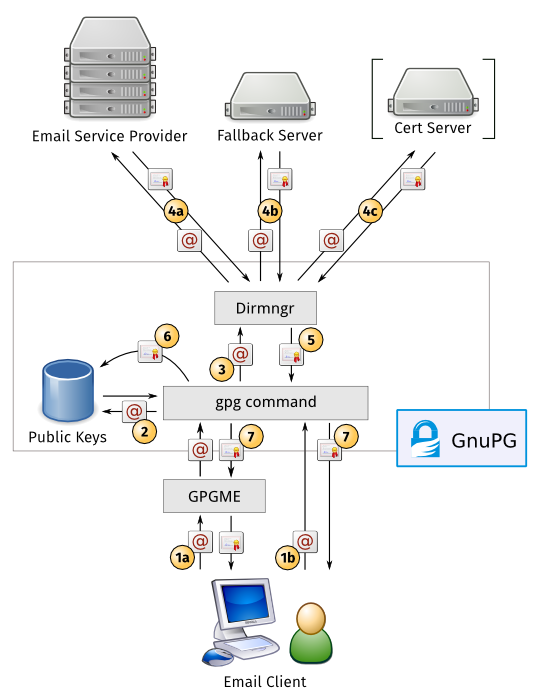
| == How EasyGPG based GnuPG backend should work? | == How should an improved GnuPG backend work? User A wants to send a signed/encrypted email to user B. The email client of A needs the certificate of B. The client asks via GpgME [1a] or directly via gpg command [1b] for the certificate with the email address of B. Gpg checks if the certificate is already in the local store of public keys [2]. If not, the Dirmngr is called [3] to ask the Email Service Provider of B [4a]. If there is no certificate the Dirmngr asks the fallback server [4b]. Only if [4a] and [4b] have no results for the requested email address the classic certificate ("key") servers are used to find a matching certificate for B [4c]. If Dirmngr gets a certificate for B it is sent back to gpg command [5] which imports it into the public key store and sends it back to the email client [7]. Now the email client can encrypt the email to B. |
| Line 19: | Line 23: |
| [[attachment:easygpg-backend.pdf|PDF]] | [[attachment:easygpg-backend.pdf|PDF]] [[attachment:easygpg-backend.svg|SVG]] |
Components
Status: Work in progress
The software components we plan to change or consider as part of the contract:
- email clients (Kontact Mail and Thunderbird with Enigmail as example for others)
- GnuPG backend
- a service located at the email service provider
- central fallback server
- classic certificate ("key") server
How should an improved email client work?
User A wants to send a signed/encrypted email to user B. A has only the email address of B. A's email client gets the OpenPGP (public) certificate from B's email service provider (step 1+2) which is used to encrypt the email to B.
How should an improved GnuPG backend work?
User A wants to send a signed/encrypted email to user B. The email client of A needs the certificate of B. The client asks via GpgME [1a] or directly via gpg command [1b] for the certificate with the email address of B. Gpg checks if the certificate is already in the local store of public keys [2]. If not, the Dirmngr is called [3] to ask the Email Service Provider of B [4a]. If there is no certificate the Dirmngr asks the fallback server [4b]. Only if [4a] and [4b] have no results for the requested email address the classic certificate ("key") servers are used to find a matching certificate for B [4c]. If Dirmngr gets a certificate for B it is sent back to gpg command [5] which imports it into the public key store and sends it back to the email client [7]. Now the email client can encrypt the email to B.